High-level overview of sprint 45
Bootstrap Peers
We started reviewing the bootstrap peers PR, ouroboros-network#4615.
Towards Typed Protocols 0.2.0.0
We discovered a performance regression when using typed-protocols-0.2.0.0, and we
started investigating where it comes from. Currently, we see that
typed-protocols-0.2.0.0 can outperform typed-protocols-0.1.0.0 when running
in isolation with a simple ping-pong protocol, so the regression might be in
the new block fetch implementation which comes with typed-protocols-0.2.0.0
See typed-protocols#3.
Tech Debt
We merged two PRs written by Galois engineers:
- a pull request which refactors the main entry function for P2P, see ouroboros-network#3834;
- a pull request which reviews usage of
unsafe function in the network code based.
Galois also made progress with the following two issues:
IO-Sim
IOSimPOR
We found and fixed a bug in IOSimPOR. We'd like to thank Prof. John Hughes
(Quviq AB) for helping us with debugging the issue.
We also provided a more uniform API for IOSimPOR, and added ways to make the
debugging similar problems in the future easier.
Technical Details on IOSim refactoring
We removed the usage of `unsafePerformIO` from `IOSimPOR`, which also means removing parallel evaluation of discovered races. We found out that it gives only 25% better performance. In the future QuickCheck will offer running different cases in parallel which should provide better performance as there are no dependencies between the evaluation of different test cases, while schedules are discovered while running which limits the possible gains from running them concurrently. The performance was not the only factor though. When using parallelism in the lazy `ST` monad we'd need to rely on memory guarantees of `STRefs`. In `GHC-9.6` they share the implementation with `IORef`s, but it might not be the case in the future.
IOSim
To prepare for the next release, we consolidate packages taking advantage of
the public sublibraries supported now both by cabal and Hackage. This is
a work in progress, io-sim#114.
Cardano Newtork Service Assurance
Galois made the following progress:
- A test run of spinning up a CNSA instance was done, as a result documentation
was updated.
- Based on the IOG code review of the CNSA code, updates to the CNSA code were
made.
- Galois has started the design for adding a CNSA analysis for "fetched bytes
over time while node is syncing".
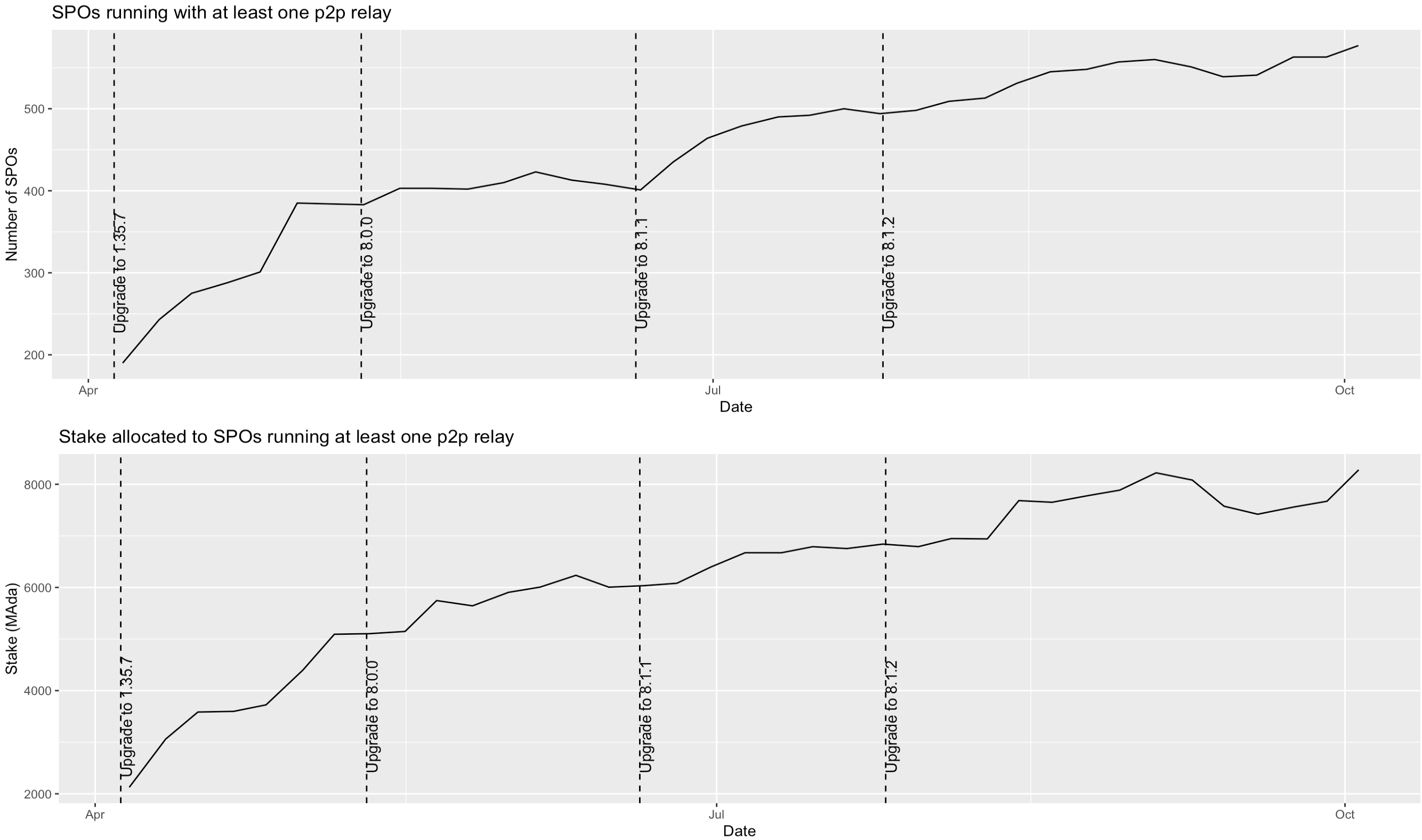
P2P adoption
In the last two weeks, we've seen increase in P2P adoption.
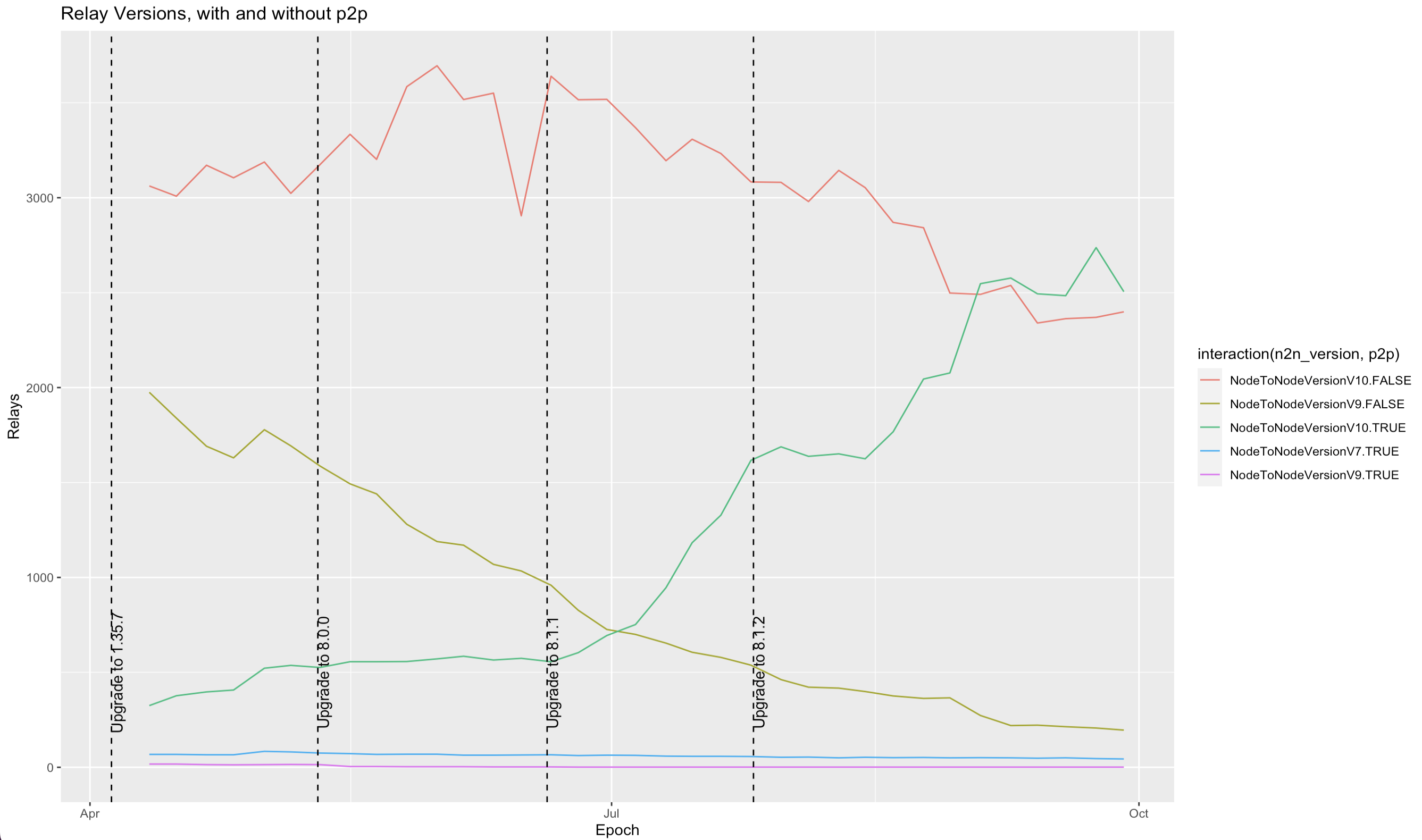
The following graphs show several different versions of relays running on the mainnet. The
green line NodeToNodeVersionV10.True denotes P2P relays.
Open Source
We upstreamed our FFI bindings to Windows named pipes to Win32 package, the
PR was accepted and merged.
We also received an external contribution which enhanced our documentation, see
ouroboros-network#4676.






