2023-04 - 2023-06
Main achievements
Eclipse Evasion
We finalised the design of eclipse evasion and implemented its mechanism which relays on connectivity to big ledger peers. Big ledger peers are the largest ledger peers which accumulate 90% of stake (currently there are less than 1000 of them). The outbound governor has new targets for known, established and active big ledger peers which work in a similar way that such targets work for ledger peers. The ouroboros-network#4662 PR is currently in review.
As part of this work we also identified a bug which would prevent a node to
connect to itself. Such connections are not easily detectable and are expected
to be dropped by the churn mechanism, nonetheless they should not be buggy.
The failure was discovered thanks to our e2e simulation of diffusion using
io-sim & property based testing.
The PR also refactors the heart of the ouroboros-network interface reducing
technical debt that would otherwise accumulate.
We also identified a possible improvement in the churn mechanism, which will be implemented in Q3. Churn needs to await for peers to terminate, we can improve the synchronisation. [ouroboros-network#4617]
Ecosystem P2P Deployment Progress
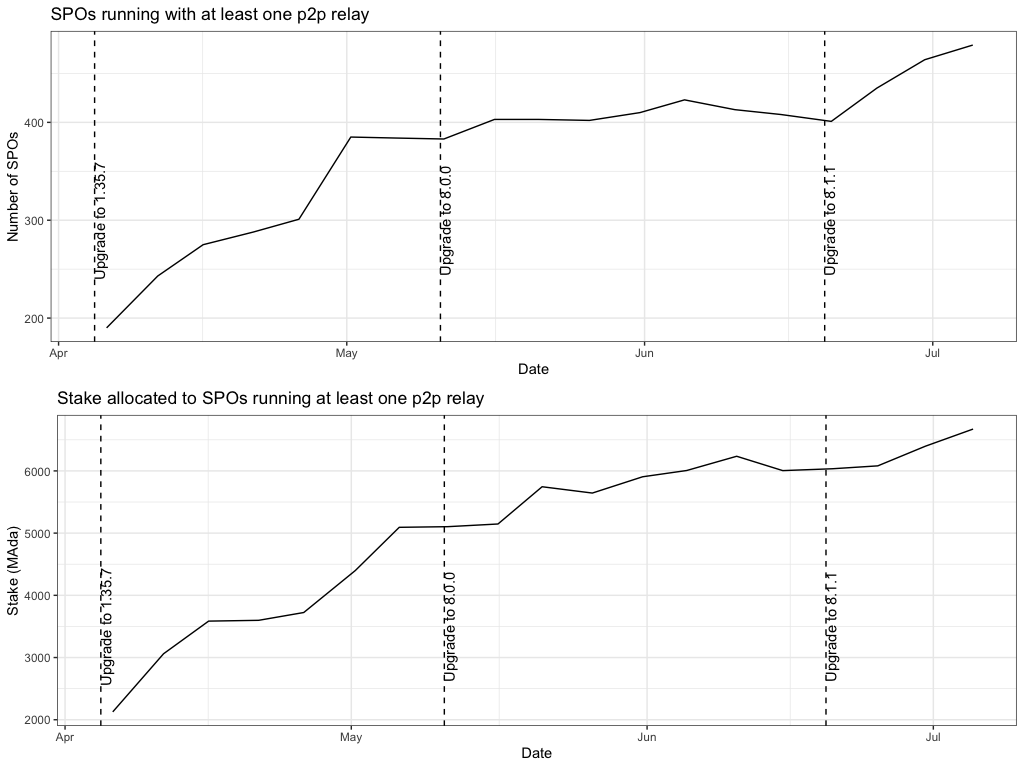
We reached 50% of stake in hands of SPOs who run at least on P2P relay. Now also Emurgo and CF are running some P2P relays. Also 20% of IOG relays are running in P2P mode.
Peer Sharing
We implemented bootstrapping for peer sharing (also known as light peer sharing). New downstream (inbound) peers are now added to the known peers of the outbound governor. Together with peer sharing this allows for non registered relays to propagate through the network. ouroboros-network#3596
Please note that peer sharing is disabled by default and is not considered safe until Bootstrap Peers (see below) or Genesis is implemented.
Diffusion (P2P)
We designed a feature which will reduce the load on IOG relays (in future also run by CF & Emurgo). The feature consists of two parts. A new source of peers called bootstrap peers (obtained from via an https request), the ability to switch from bootstrap peers to ledger peers if the node is synced (we are collaborating with the consensus team on the interface Bootstrap Peers IER). This feature will be completed in Q3. ouroboros-network#4530
We published a blog post about P2P design & implementation.
Karl Knutsson (CF) fixed an issue observed on a relay with a lot of outbound connections: ouroboros-network#4559.
We merged changes which allow the consensus layer to start / stop block forging thread. This will allow to deploy P2P block producing nodes which serve as a live backup node. ouroboros-consensus#140
We fixed a few bugs in local root peers DNS resolution service: ouroboros-network#4583, ouroboros-network#4571.
We limited concurrency of DNS name resolutions: ouroboros-network#4596.
Galois Inc implemented query option for Handshake: ouroboros-network#4256.
We fixed handshake query timeout: ouroboros-network#4608.
We implemented warm valency for local root peers. This can help when using DNS names in local root peers which resolve to many IP addresses. ouroboros-network#4575
We merged handshake changes which allow query protocol versions. Thanks to James Parker from Galois Inc.: ouroboros-network#4256, cardano-cli#30.
Other Improvements & Developments
CDDL
We added
node-to-nodeandnode-to-clientCDDL specs / tests for encoding ofNodeToNodeVersionDataandNodeToClientVersionData.We clarified an inconsistency between CDDL spec and implementation which is highly polymorphic. We designed and implemented a fix for
tx-submissionandlocal-tx-submissionmini-protocols. Specs for other mini-protocols will be improved at a later stage. ouroboros-network#4580
Cardano Ping
cardano-pingcommand was deprecated in favour ofcardano-cli ping(the transition was done by thenodeteam).Support for
node-to-clientprotocol using Unix sockets. ouroboros-network#4601Support for
NodeToNodeV_11andNodeToClientV_16, ouroboros-network#4587cardano-cli pingis now using ISO8601 format for timestamps. Formatting of messages was improved. ouroboros-network#4593cardano-cli pinghas a new--query-versionsflag which allows to query supported versions by the remote node. This is supported bycardano-node-8.1.0. ouroboros-network#4589, cardano-node#5313, cardano-cli#30
IOSim
We fixed timeouts & delays in
io-classesin a series of PRs: io-sim#81, io-sim#82, io-sim#86, io-sim#87.We released
strict-stm-1.1.0.1on Hackage which fixed a bug in package description file: io-sim#101.
Typed Protocols
- We published haddocks of
typed-protocolsat https://input-output-hk.github.io/typed-protocols
Cardano Client
- We fixed a bug in
cardano-client-0.1.0.2release which results in clients (e.g.db-sync) negotiate an experimental protocol version.
Technical debt
After the split between consensus & network, we made
cardano-clientindependent ofouroboros-consensus-diffusion: ouroboros-network#4526.We wrap all exceptions in
DiffusionError: ouroboros-network#4537, cardano-node#5356.
CI improvements
We switched to use GitHub merge queues in
ouroboros-network,io-simandtyped-protocolsrepositories; typed-protocols#30, ouroboros-network#4546.We cleaned & updated scripts which run on CI.
We implemented a script to verify & release packages on CHaP; ouroboros-network#4542, ouroboros-network#4573.
We implemented a new CI script and cleaned existing ones: ouroboros-network#4572.
We don't install cryptographic libraries on CI anymore as none of our packages requires them; ouroboros-network#4539.
Improved caching of dependencies: ouroboros-network#4553.
We made it possible to trigger building haddock manually: ouroboros-network#4549.
GHC 9.4 & 9.6
We made all repositories under our control compile with ghc-9.4 and ghc-9.6
which includes ouroboros-network, io-sim, typed-protocols and
Win32-network.
Next steps
We will continue towards our aspirational roadmap.
- We will continue reviewing eclipse evasion.
- As ouroboros-consensus#140 was merged, we are making progress towards releasing P2P on block production nodes. We hope to analyse performance regression on such nodes observed on the benchmarking cluster. roadmap-3887
- We are also focused on roadmap-3969. Note that it was expanded in Q2.
